Professional Experience
All through my career, I managed to successfully combine my professional skills with my personal interests. My projects, showcased below, are a window into my world: creative, varied, and engaging. They capture my professional development as well as some special experiences.
On-the-Job
Exciting news ahead… stay tuned!

Stay tuned…
Driving Security and Compliance at a Tech-Startup

Engineered security solutions, crafted technical policies and drove implementation amongst cross-functional teams, ensured compliance with NIST 800-53 controls, proactively fortified security posture, and revamped the supply-chain/procurement process resulting in over $500k cost savings.
Threat Intelligence in Both the Public and Private Sector

“Threat intel drives detect and response”, a co-worker previously told me. We need to know what the bad guys are doing to build-out detections to flag observed anomalous activity. Utilizing various available intel feeds, led initiatives to integrate feeds with security products, significantly amplifying visibility of potential cyber threats.
Internet of Things (IoT) Upgrade and Improvements

Worked with cross-functional teams to build and implement an IoT policy. Engineered a secure solution to upgrade the Agency’s Building Management Solution utilizing industry best practices.
Building and Leading Security Operations at the DoD

Utilized industry best-practices such as MITRE ATT&CK and NIST, developed Agency Incident Response Plan (IRP), playbooks, and table-top exercises to improve detection and response capabilities. Led a team of 40 personnel to ensure efficient 24×7 operations of the security operations center.
Building a Vulnerability Management Program at the DoD

Orchestrated the remediation of over 25,000 critical and high severity vulnerabilities. Improved efficiency in remediation process by automating procedures for scanning and reporting vulnerabilities reducing the response time for addressing newly published vulnerabilities.
Coursework
Certified Information Systems Security Professional (CISSP)

Gained knowledge and skills to lead an organization’s information security program.
CompTIA Cybersecurity Analyst (CySA+)

Demonstrated knowledge in threat detection, incident response, and vulnerability management.
Cybersecurity Maturity Model Certification – Lead CCA
Completed training in the CMMC framework, including scoping, evaluating, and validating compliance against NIST SP 800-171. Developed skills to lead assessment engagements and guide organizations toward audit readiness.
Offensive Cyber Operations

Deployed Kali Linux and used known exploits to attack classmates in a lab environment. Successfully attained root shells on numerous machines, and maintained access.
Defensive Cyber Operations

Tasked with creating Windows and Linux systems, creating users and services, and hardening to the best of our ability, worked with a team to defend against professional red-teamers. Monitored the systems for unauthorized access throughout the entire exercise.
Reverse Engineering/Malware Analysis
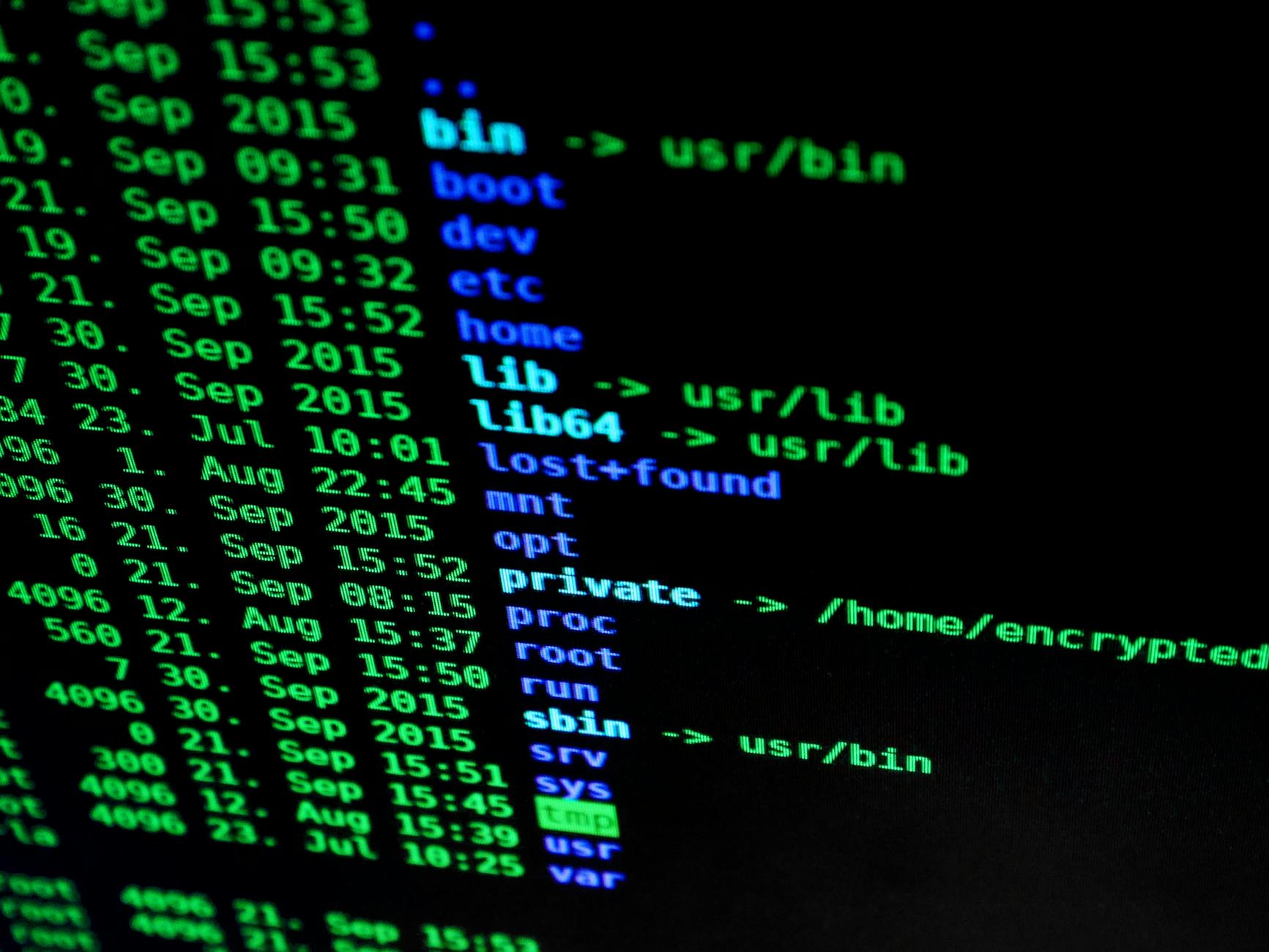
Analyzed njRAT, a remote access trojan. Performed static and dynamic analysis, and examined import functions, DLLs used, and other behavior. In addition, disassembled the malware to examine assembly code.
Analyzing Vulnerabilities in Pacemakers

Today, pacemakers are constantly sending and receiving information from the patient to their doctor. While convenient, this introduces risk. I examined how secure pacemakers really are, and the potential attacks one may use that can lead to potentially fatal consequences for the patient.
Building a Raspberry Pi Security and Motion Camera
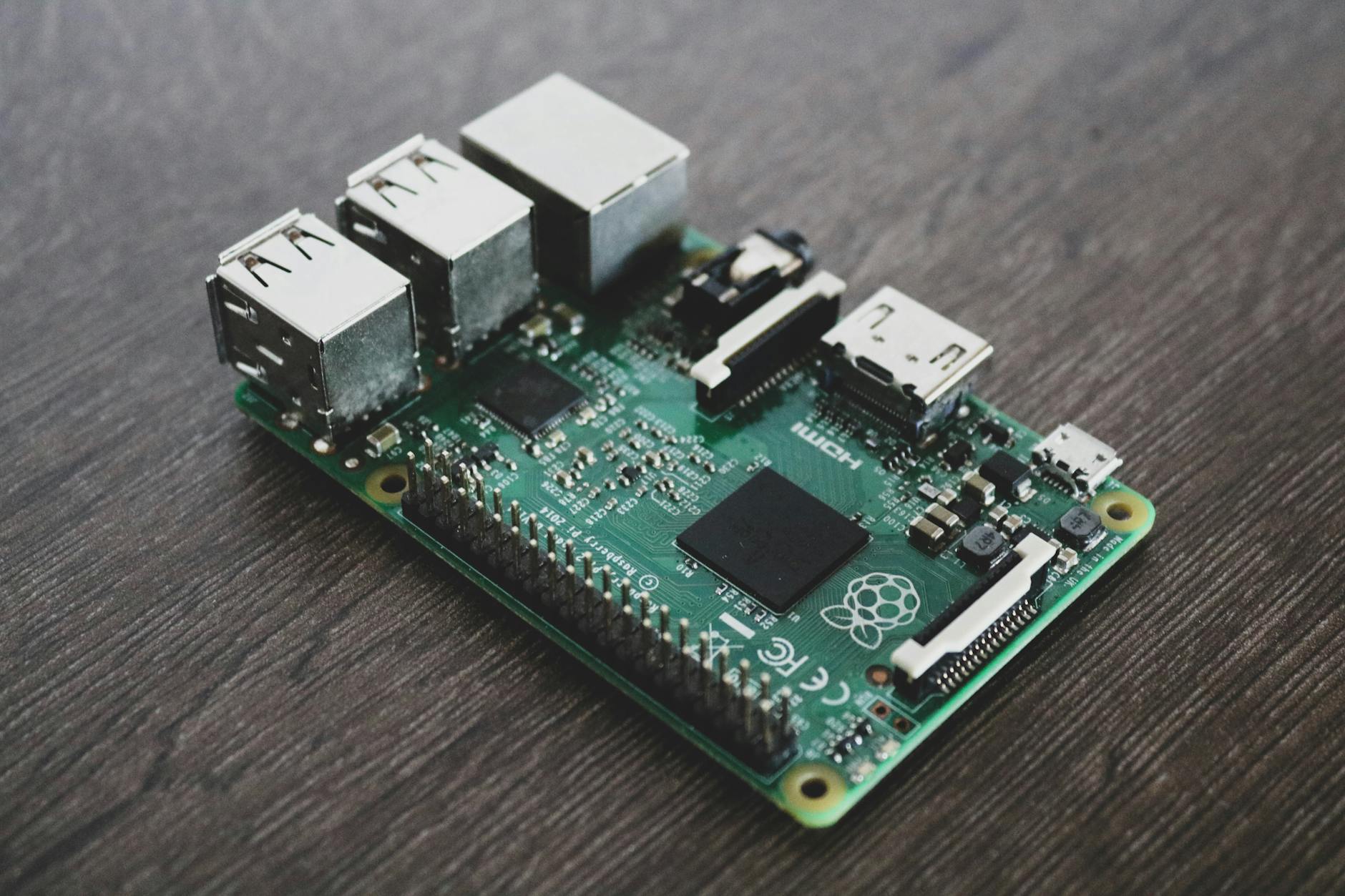
Using Raspbian, an open-source Linux distribution for the Raspberry Pi as well as Motion, an open-source library for the security camera feature, I configured SSH and dynamic DNS to allow a user to type in the name of their Raspberry Pi from a remote device and access the footage from a far. This allowed a user to monitor their camera footage when away from their home.
Programming a Website Using Ruby on Rails

The goal… to reinvigorate the public’s interest in national parks. Using the National Park Service’s (NPS) API, I was able to pull park information into a database to use for my site. Users were able to create campsite bookings, play trivia, and even donate to their favorite park using Stripe’s API.
Copyright 2025 Daniel M. Elice